Introducing A Turbocharged Alert Search Experience
Hello Kentik Users
Ever felt like you were searching for a needle in a haystack of alerts? We get it. When you need to find a specific alert, you need to find it now. That's why we're thrilled to announce a massive power-up to the search bar on the Alerting page!
What's New?
Previously, your search was limited to the Alert Policy name and its dimensions. While useful, we knew it could be better. You can now use the search bar to find alerts based on any information contained within the alert details.
Just type what you're looking for, and we'll scan everything. This includes, but is not limited to:
- Site names or geographic locations
- NMS device details like manufacturer or model
- Alert Policy labels
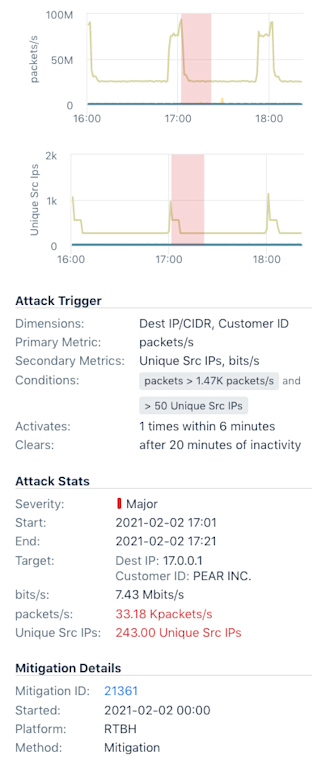
- Specific IP addresses, ASNs, or tenants
- Mitigation IDs or Alert IDs
Why You'll Love It
This enhancement is all about speed and precision, helping you slash the time you spend managing alerts.
- Find What You Need, Faster: No more clicking through complex filter combinations. Instantly pinpoint the exact alerts you're looking for with a simple text search.
- Deeper, Quicker Investigations: Need to find all "Critical" alerts from your "Cisco" routers in the "Ashburn" site? Just type it in. Troubleshooting has never been this easy.
- Improved Workflow: Spend less time hunting and more time resolving. This intuitive search experience streamlines your entire incident response process.
Jump into the Alerting page today and take the new, supercharged search for a spin.
Happy searching!